
What is the MITRE ATT&CK Framework?
Created by MITRE in 2013, ATT&CK serves to document attacker tactics and techniques from real-world observation in an attempt to solve problems.
Open and available to everyone, the framework encourages security organizations and vendors to map their capabilities to the techniques and tactics in this framework in order to improve our collective cyber defence capabilities.
It is now widely recognized as an authority on understanding the behaviours and techniques of the world’s most dangerous cyber threat actors – But what is it exactly?
Read on below to find out:
Mitre ATT&CK Breakdown:
Successful threat detection typically requires that an organization have a deep understanding of the most common techniques and tactics used by threat actors, as this ultimately allows defenders to prioritize which ones pose the greatest threat to your organization.
Unfortunately, the sheer volume and breadth of adversarial tactics available to attackers mean that it would be nearly impossible for any single organization to map out and catalogue each one, let alone defend against each one adequately.
This framework is a knowledge base that indexes and breaks down in detail the exact steps and methods that hackers use, which ultimately allows security teams to understand the actions required to protect themselves.
MITRE ATT&CK Matrix:
Since it’s inception in 2013, the ATT&CK framework has since been split into three different versions:
- Enterprise: Windows, Mac, Linux
- Mobile: iOS and Android operating systems
- Pre ATT&CK: Prepatory Techniques
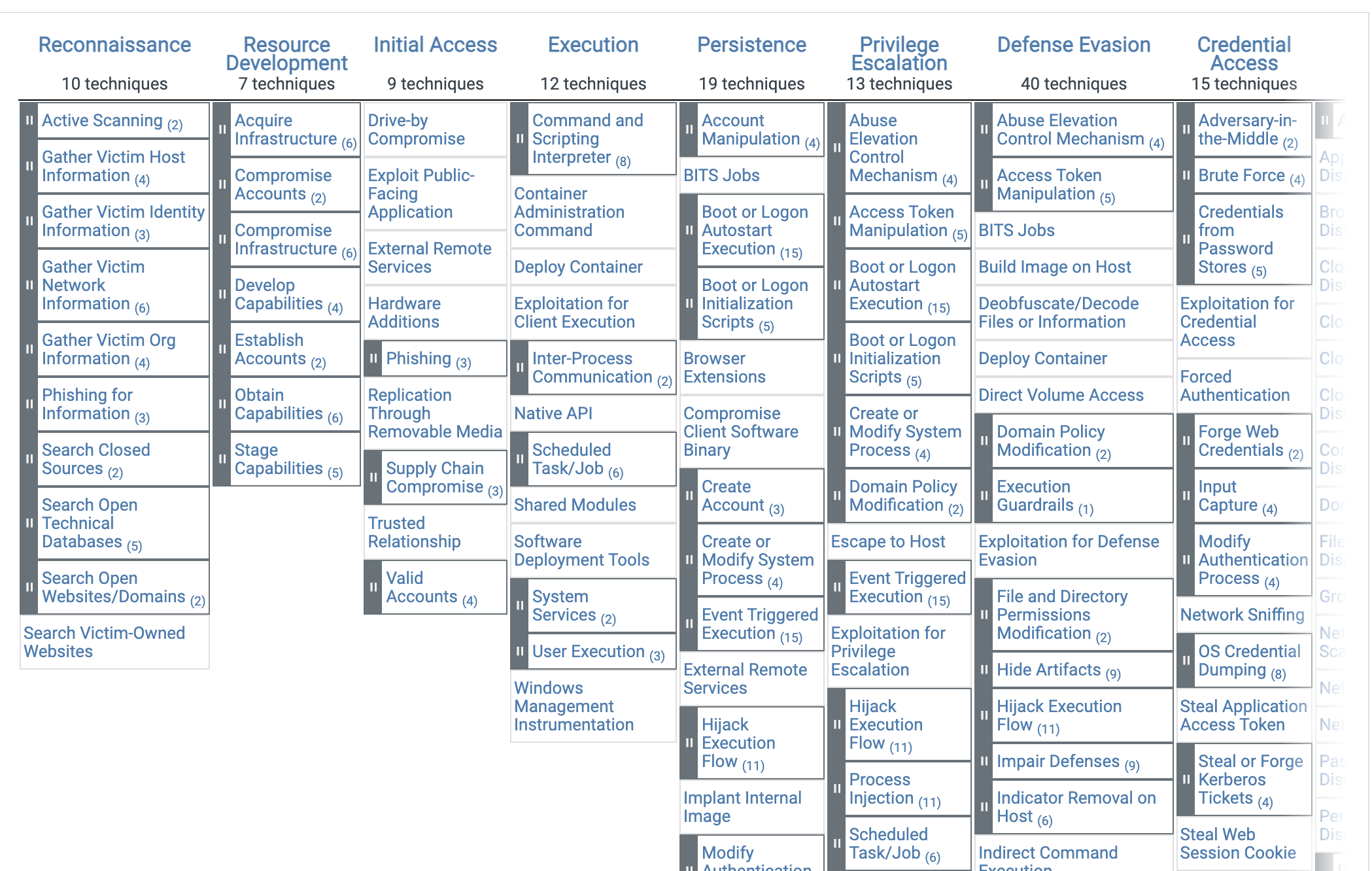
The enterprise version of the ATT&CK Matrix has 14 different tactics:
- Reconnaissance: Gathering information for future adversary behavior
- Resource Development: resources to support security operations
- Initial Access: Attempting to break into your network
- Execution: Trying to run the malicious code (remote access tools)
- Persistence: Trying to maintain their foothold
- Privilege Escalation: Trying to gain higher level permissions (using existing tools to escalate access)
- Defense Evasion: Avoiding detection
- Credential Access: Stealing account names and passwords
- Discovery: Finding more compromised systems to target
- Lateral Movement: Moving through your environment
- Collection: Gathering relevant data (Accessing data in cloud environments)
- Command & Control: Taking control of compromised systems
- Exfiltration: Transferring/stealing data
- Impact: Manipulate, interrupt or destroy data and systems (Inhibit response function)
For each of these tactics, the Mitre ATT&CK lays out the set of techniques used by malware and threat groups.
Currently, there are about 185 techniques and 367 sub-techniques, with more being added continuously.
Each of these allows defenders to better understand how to defend against different tactics and adversary tactics.
Why is ATT&CK Relevant to your Organization?
Mapping and cataloguing every single technique used by threat actors is a monumental task, which begs the question – What is the point?
MITRE ATT&CK is widely recognized as an authority on understanding behaviours and techniques. This ultimately removes ambiguity and provides a common vocabulary for industry professionals to discuss and collaborate.
Additionally, there are also many practical applications that the ATT&CK Framework provides, including:
- Prioritize Detection Based off Your Organization’s Unique Environment: Preparing for every attack vector is impossible. This framework allows teams to determine where to focus their detection efforts and which adversary tactics are being used.
- Evaluating Current Defenses: The ATT&CK framework can serve as a great tool for evaluating the depth of coverage around key attack techniques, as it clearly defines which threats are a priority for an organization. This in turn allows security teams to check how their current coverage stacks up in real-world observations.
- Tracking The Latest Threats: The ATT&CK framework is not a static document and will continue to track specific adversary group behaviours. Ultimately it is a useful source of truth for security operations teams to understand the movements of hacker groups and the techniques they use.
MITRE ATT&CK vs. Cyber Kill Chain
If you pay attention to cybersecurity, you may have heard about another framework for understanding adversarial behavior and tactics called the Lockheed Martin Cyber Kill Chain.
In contrast to MITRE ATT&CK, this model contains the following steps presented in sequence:
- Reconnaissance: Harvest email addresses, information, data
- Weaponization: Couple exploit with a backdoor into a deliverable payload to gain access
- Delivery: Deliver weaponized bundle to the victim via USB, Email, Web…etc
- Exploitation: Exploits vulnerability to execute code on a target network or system
- Installation: Install malware on a target
- Command & Control (C2): Create a command channel for remote manipulation
- Actions on Objective: Accomplish original goals
MITRE ATT&CK and Cyber Kill Chain – Key Differences
In short, the MITRE ATT&CK framework goes into much more depth and detail through its various techniques and sub-techniques detailed within. MITRE adversarial tactics are constantly being updated to ensure that defenders are able to update their own tactics accordingly.
Additionally, the Lockheed Martin Cyber Kill Chain does not factor in the different cloud-based tactics and techniques used by threat actors. This framework assumes that a threat actor will deliver a malware payload to the system, which is not very relevant for cloud-based attacks.
Stratejm & Mitre ATT&CK
Stratejm’s security team is always participating in MITRE ATT&CK discussions and events, with extensive experience in performing machine learning-based anomaly detection in our arsenal.
We highly recommend that every organization incorporates this framework, and are happy to help those who need it.
Contact us today for a consultation to find out how we can help map your security practices against the MITRE ATT&CK Framework.

